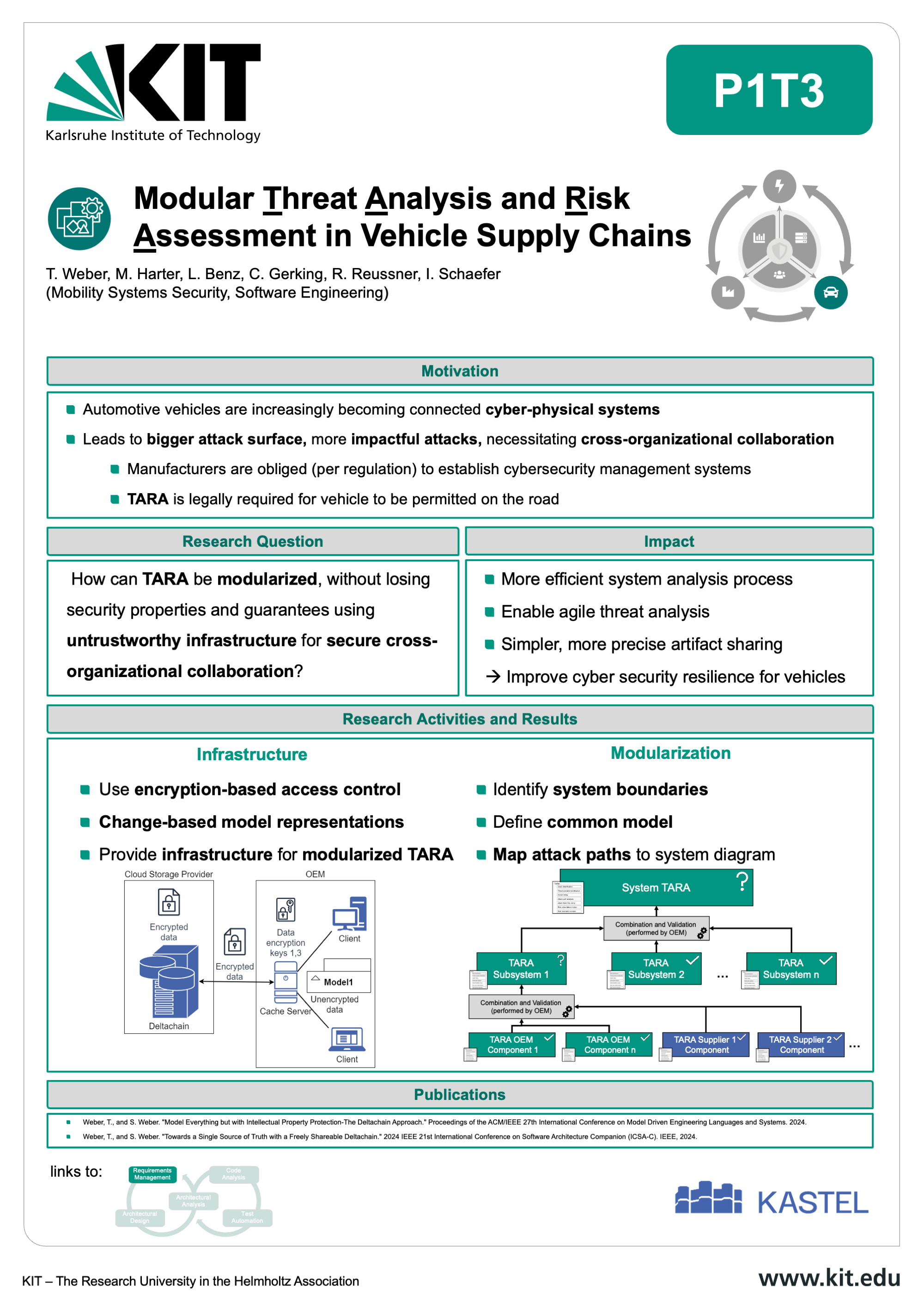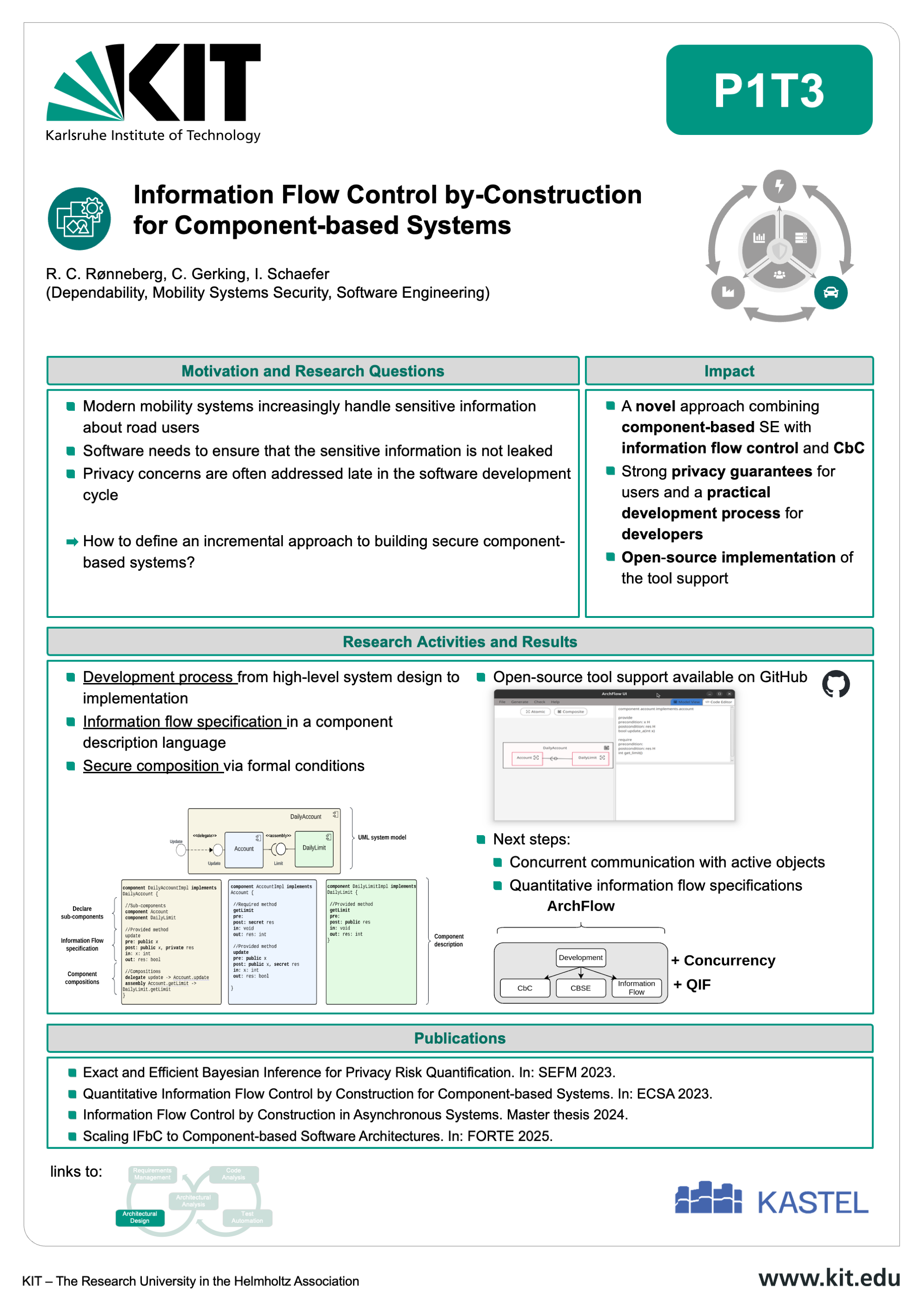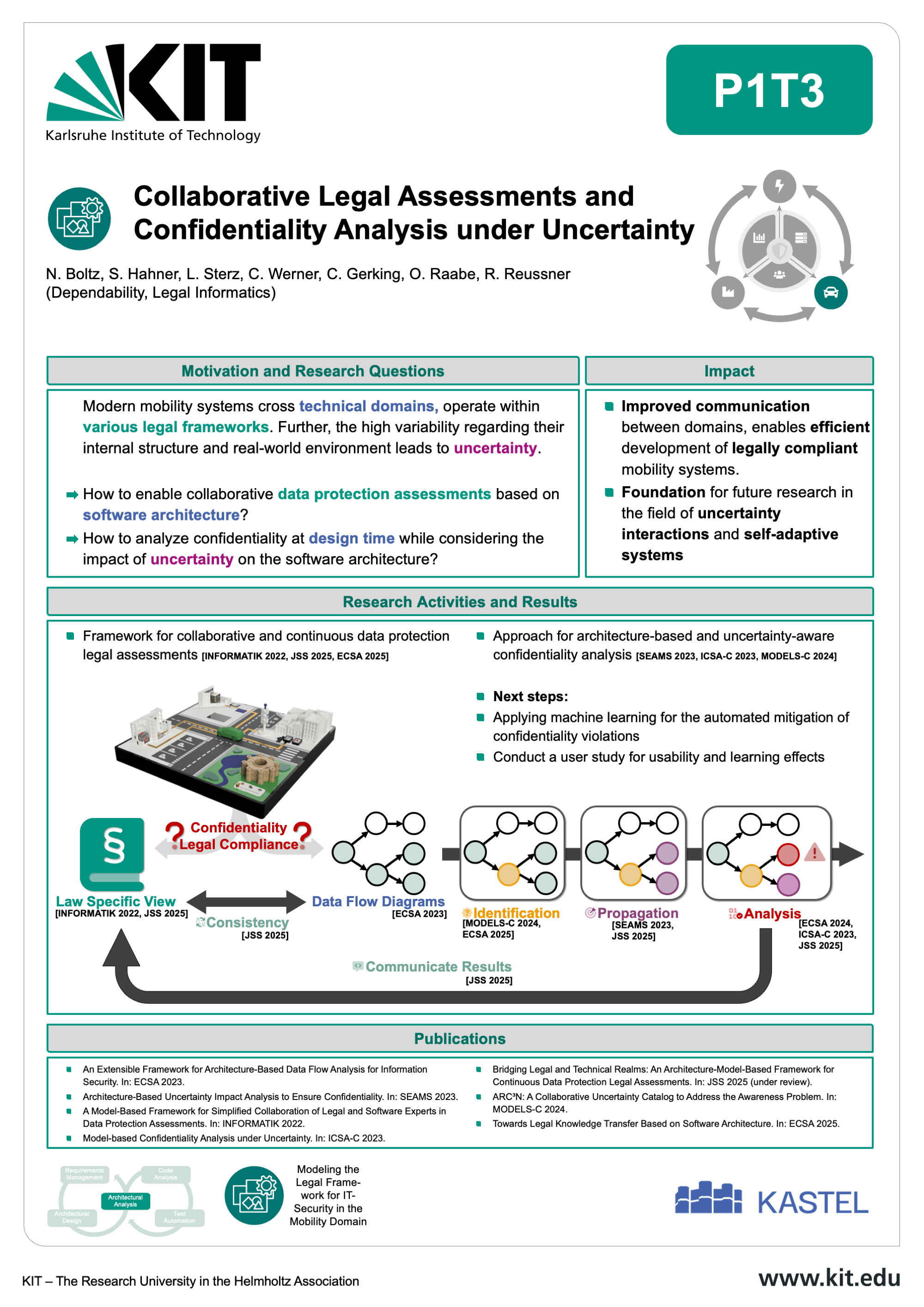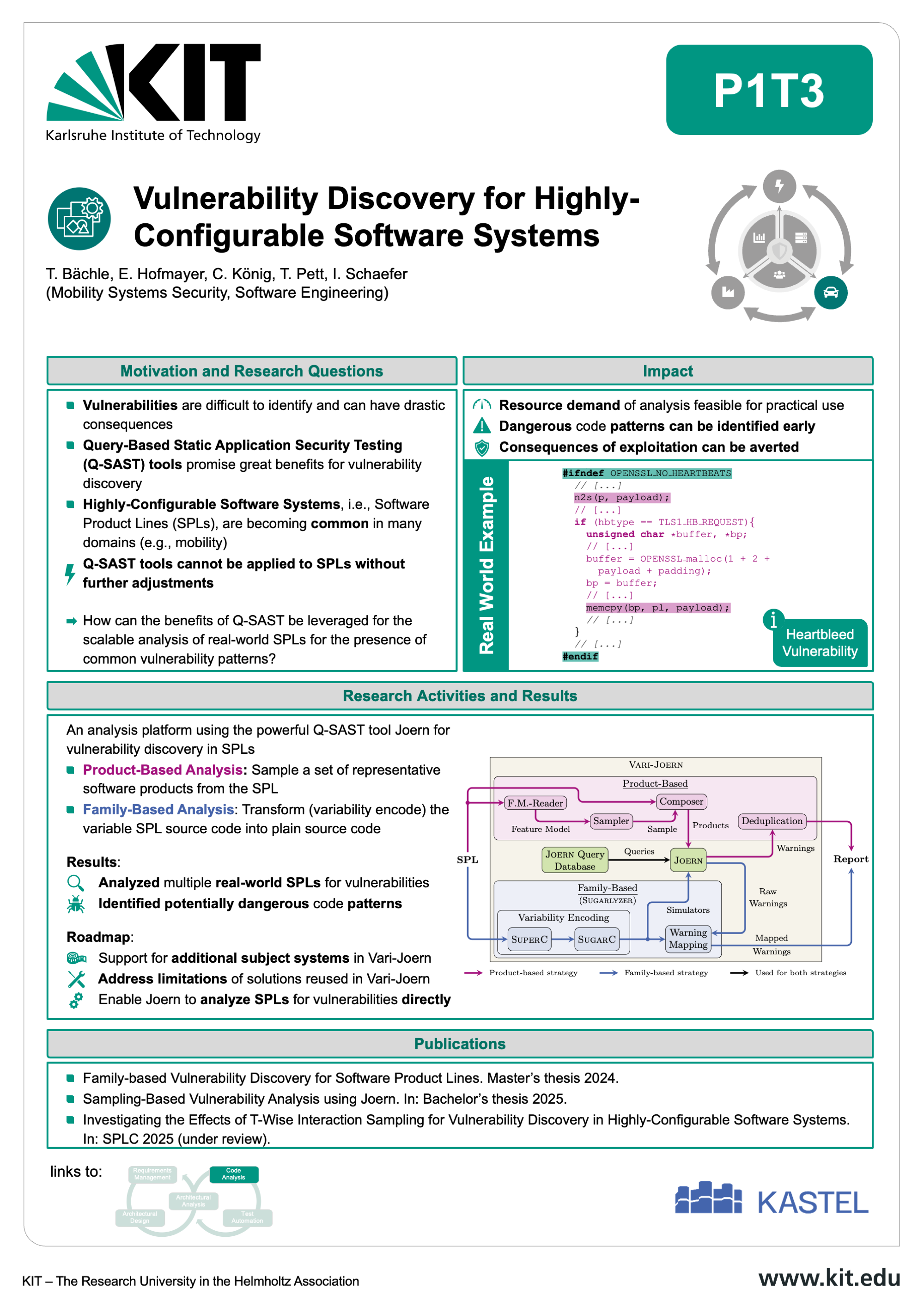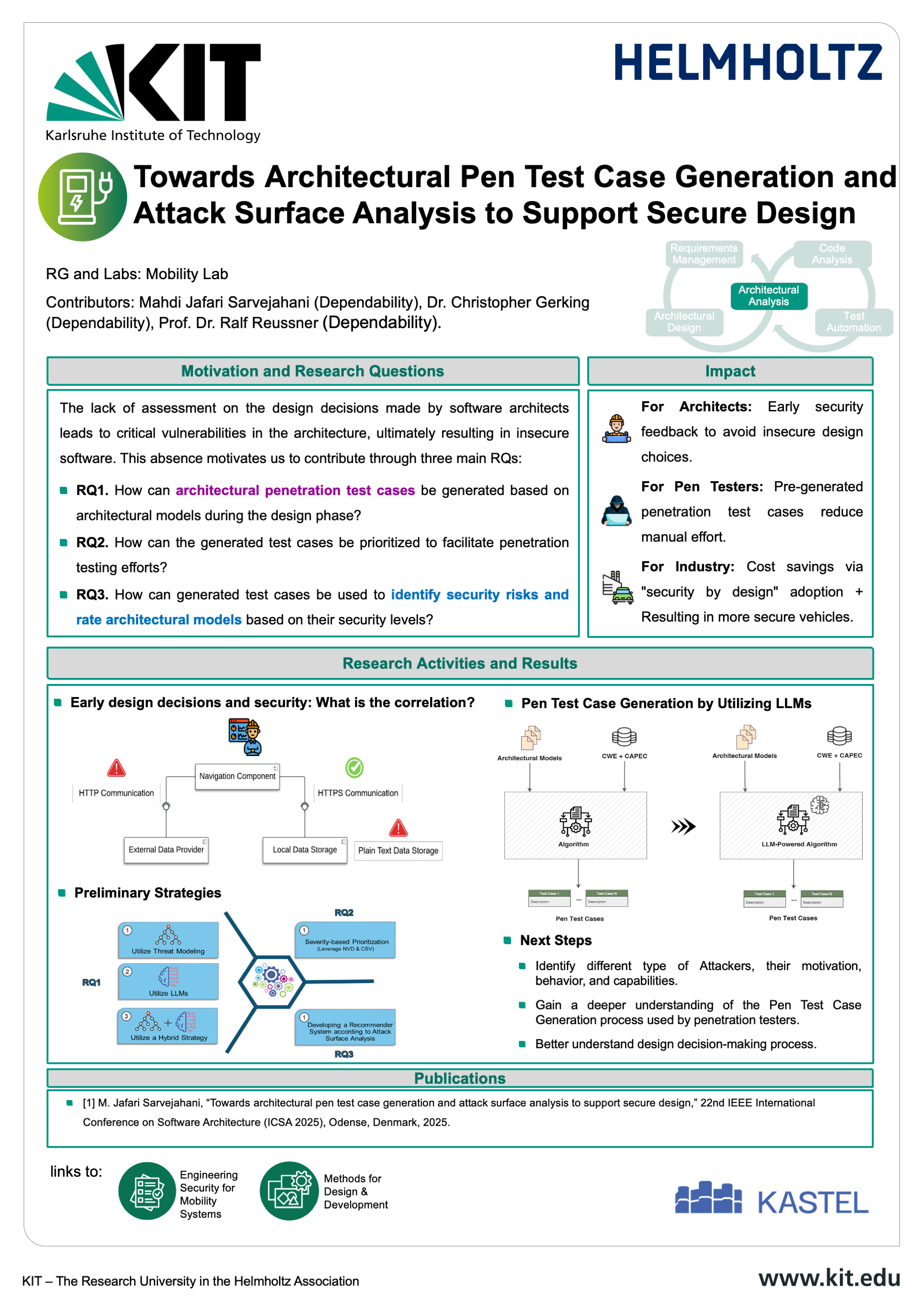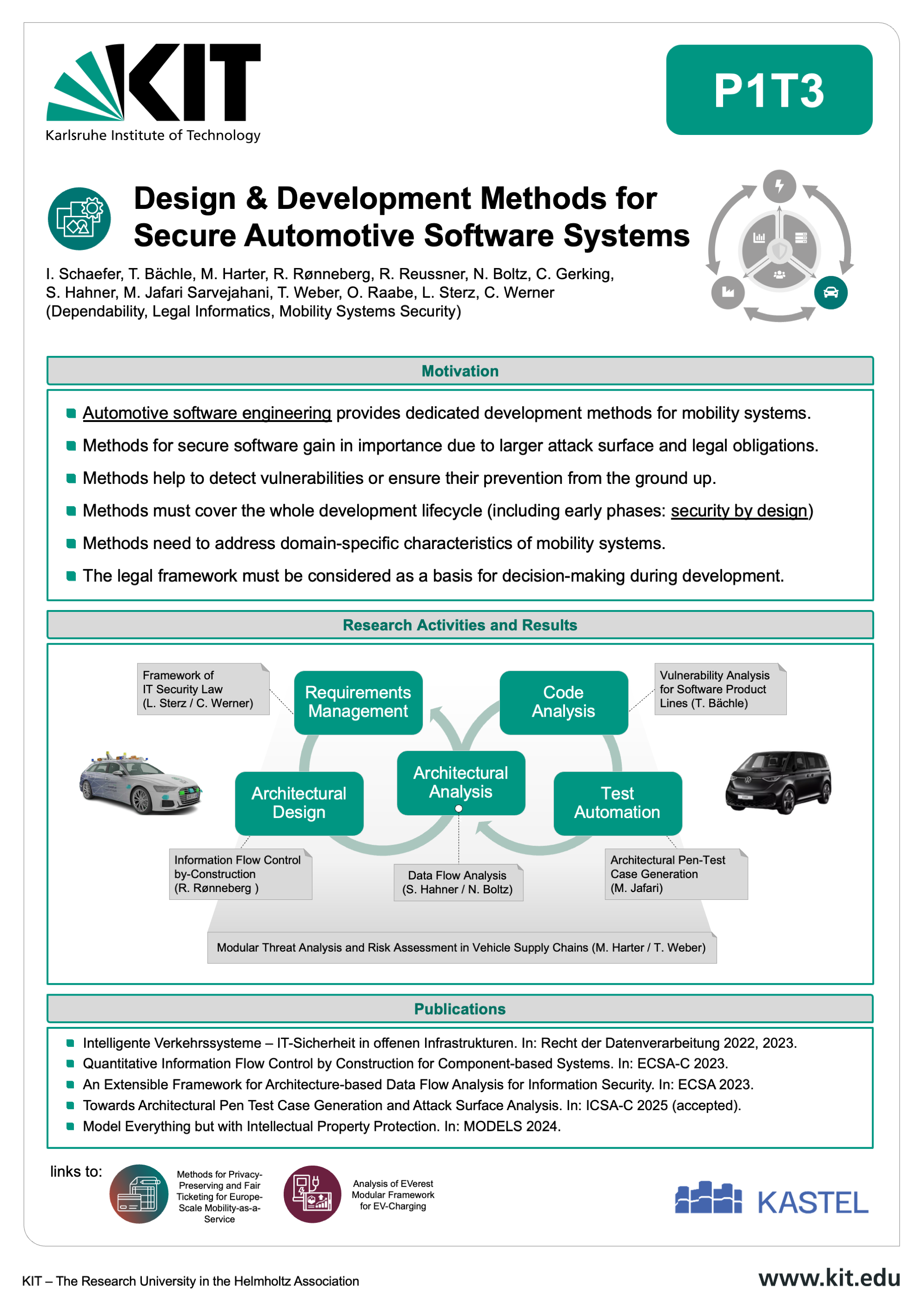
The Mobility Lab aims at developing robust, secure, and legally compliant software systems for the next generation of connected and autonomous vehicles. As the complexity of mobility systems grows, so does the potential attack surface — making cybersecurity a critical priority across the entire automotive software lifecycle.
Our research at the Karlsruhe Institute of Technology (KIT) focuses on dedicated design and development methods tailored to the specific needs of automotive applications. These include early-stage security-by-design principles, advanced architectural analysis, automated code analysis, and domain-aware test generation. By addressing vulnerabilities from the ground up, we aim to create software that is not only functional but also resilient against emerging threats. The Mobility Lab brings together interdisciplinary expertise in automotive software engineering, IT security law, and mobility systems to ensure that technical development aligns with evolving legal and regulatory requirements. This includes frameworks for secure requirements management, information flow control, and architecture-based risk assessment. Through close integration of research activities — from requirement engineering to testing — the lab supports a seamless and secure development process for future mobility platforms. The outcomes contribute to areas such as secure EV charging infrastructures and privacy-preserving mobility services. By combining innovation with legal awareness, the Mobility Lab is helping shape a safer digital future for transportation.
Learn more about the results, publications, and collaborative tools by exploring the individual contributions below.